Features of iPSK:-
1.Unique PSK for individual Client/Groups.
2.Easy to revoke the PSK, if gets compromised without affecting the other groups.
3. Easy to track down and mitigate the affected PSK group.
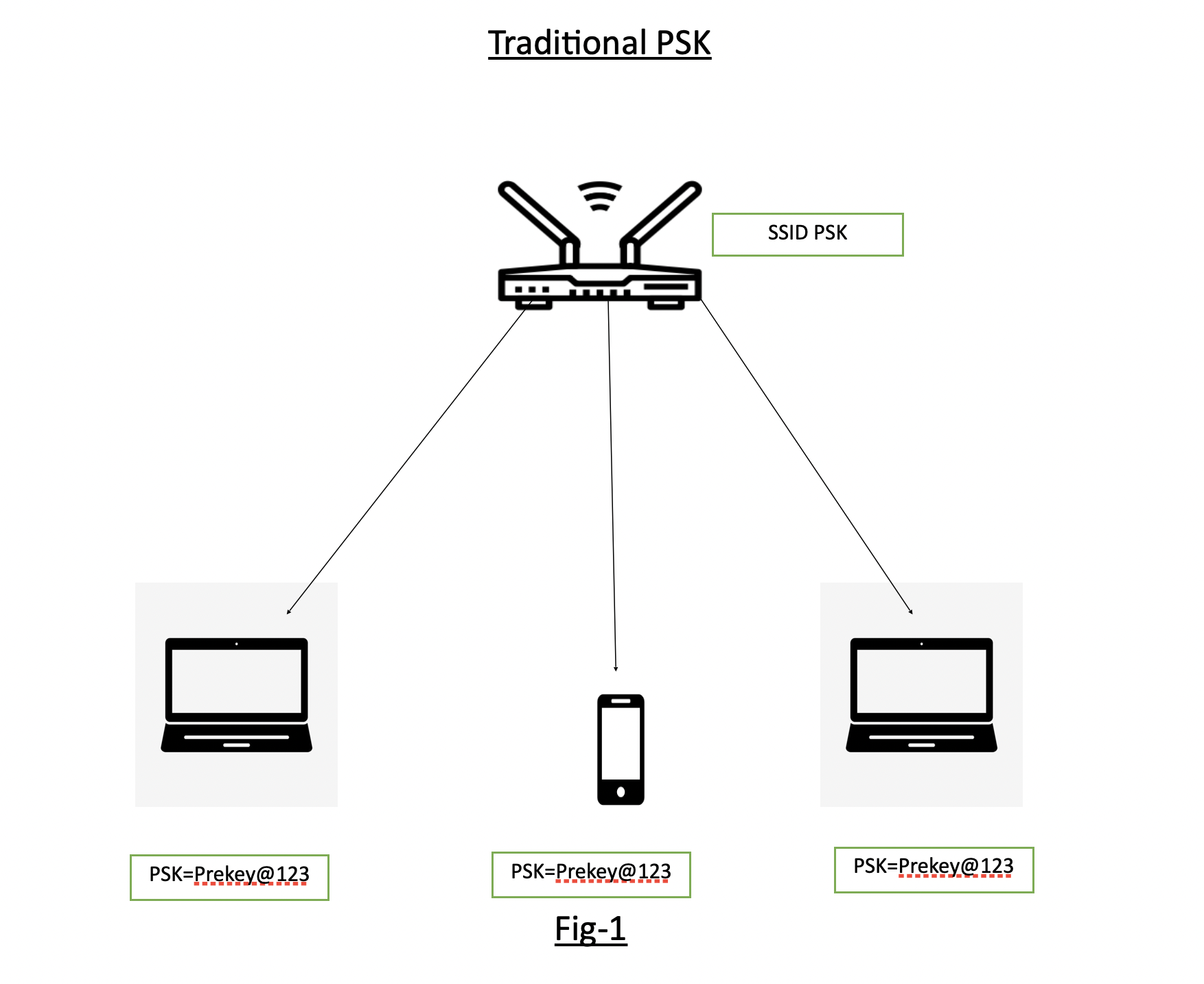 Fig-1 shows the traditional PSK where SSID “PSK” is having the Pre-Shared Key as “Prekey@123” and is distributed to all devices connecting to it.
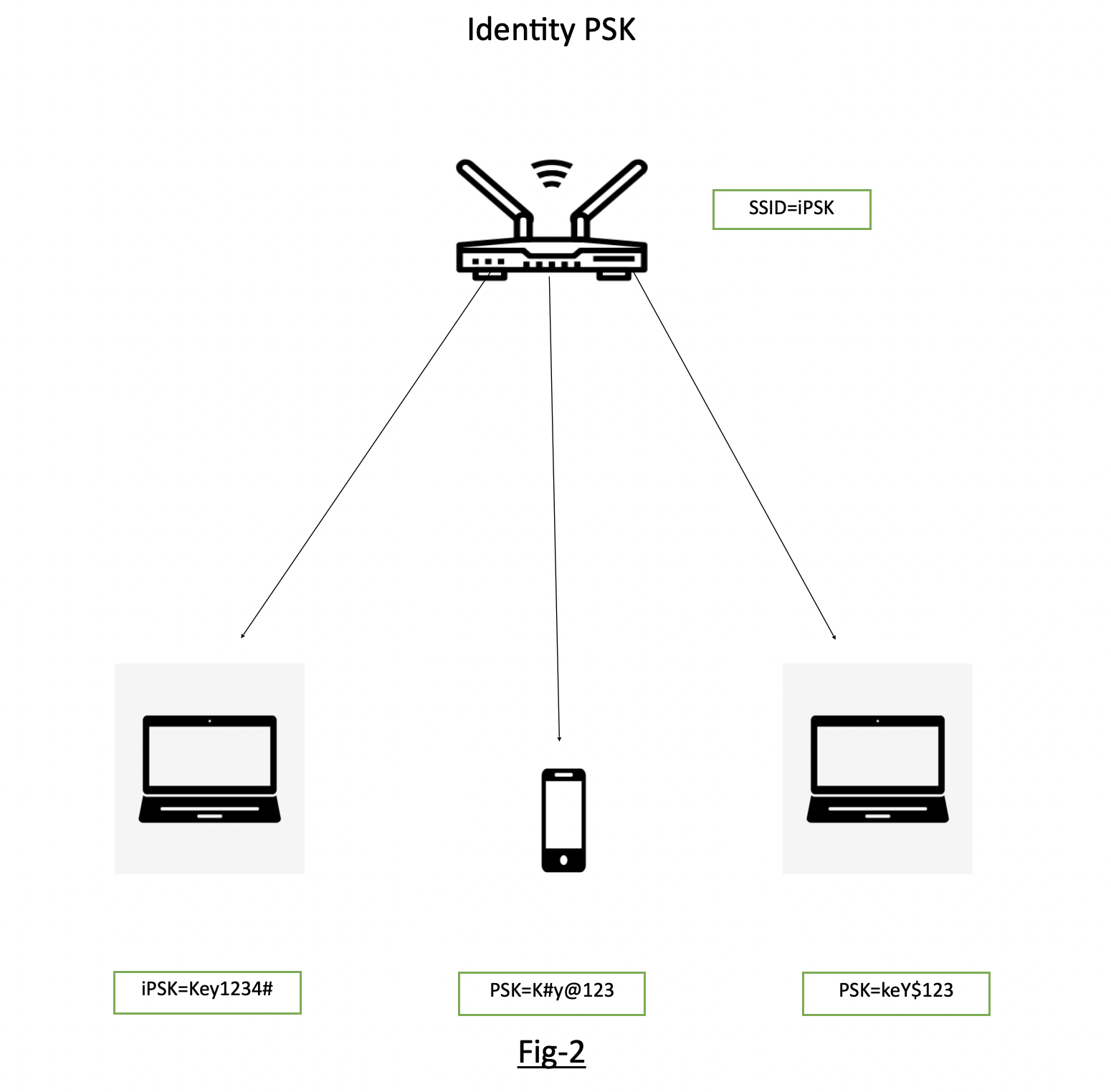
Fig-1 shows the traditional PSK where SSID “PSK” is having the Pre-Shared Key as “Prekey@123” and is distributed to all devices connecting to it.Fig-2 showing the SSID “iPSK” configured and different devices are being connected to the same SSID iPSK with individual keys.
Pre-requisites for Identity PSK in CISCO environment
- Wireless LAN controller (version 8.5 or later)
- Identity services engine (version 2.2 or later)
- Lightweight Access point
- Identity PSK WLAN
Fig-3 showing the flow of iPSK WLAN and the necessary configuration on WLC and Radius.
Implementing iPSK in Cisco wireless environment:-
Configuration of WLC
Step1- Addition of Radius Server. Go to Security>AAA>Radius Authentication. (i.e., adding details of ISE, which is a radius server in this example)
Step2- Creation of Identity PSK WLAN
Step3- Edit WLAN, Layer-2 choose WPA2 Policy>PSK and check MAC Filtering
Step4- Choose Radius (ISE) Server under Security>AAA Servers
Step5- Check Allow AAA Override under WLAN Advanced
Now, we have two scenarios --
i. Separate PSK for individual mac address
ii. Common PSK for a group of devices and multiple device groups across a single WLAN
Case1- Creation of Authorisation policy based on individual MAC addresses
Configuration on Radius (ISE)
Step1- Adding NAD (Network Access Device) like WLC. Go to Administration>Network Resources>Network Devices>Click Add.
Step2- Create an authorization profile under Policy>Policy Elements>Results>Authorisation Profiles.
Step3- Create Authorisation rule for individual users on basis of MAC address
Step1- Create different endpoint groups for a set of different devices under Administration>Groups>Endpoint Identity Groups
Step-2 Create different Authorisation Profiles for different device groups under Policy>Policy Elements>Authorization>Authorization Profiles
Devices having MAC addresses under group G1 will have to connect with WLAN-iPSK with key=”nkn@1234” and Devices MAC addresses under group G2 will have to connect with WLAN-iPSK with key=” Tech#123”
Step-3 Creation of separate Authorization profiles under Policy>Authorization